Japanese Feature Phone Preservation

Japanese feature phones is a category of mobile devices that were released (almost) exclusively in Japan between approximately 1999-2015. These phones contained many features that took over a decade to reach the rest of the world: game streaming, live TV, digital wallets, virtual characters to replace you on video calls, and more. The phones offered platform-exclusive games from many beloved franchises such as Final Fantasy, Pokemon, Kingdom Hearts, Professor Layton, and Megami Tensei. Mobile devices in Japan were developed by a variety of companies, each with their own proprietary hardware and software. Because of the diversity of phone models, the restrictive copyright protections, a separate set of proprietary internet protocols, and more, these phones and their games have been extremely challenging to preserve.
Mobile Device Data Extraction Projects
Some Japanese feature phones can have their data extracted using the ktdumper scripts available on GitHub, along with a FOMA debug cable (a FOMA cable with pins 8, 9, and 10 bridged together). Information on creating a debug cable can be found here.
To see models that are currently compatible with the script, check out the devices.py file in the KTdumper project. There may be more models compatible that the ones listed, but these models are essentially guaranteed to work.
NEC, Panasonic, Casio
NEC
NEC devices enter a testing mode when plugged into a PC using a debug cable. Currently known exploits for NEC devices work with phones that have NEC M2 and NEC M3 CPU chips (note this is not the same as the Apple M2). Some phones with OMAP chips are also preservable (OMAP 1610, OMAP 1621?), but later phone models still require more study (OMAP 3430).
Panasonic
For Panasonic phones, the debug cable triggers Panasonic IPL mode.
Some Panasonic phones have also had their firmware extracted by unsoldering the eMMC and analyzing it with a chip programmer.
We have extracted data with Panasonic phones that have the following CPUs:
- OMAP 1610
- OMAP 1611
- OMAP 2420
- UniPhier 3M
- UniPhier 4MBB +
Progress was halted on Panasonic phones for a while due to difficulty in deciphering the FTL (Flash Translation Layer), but this has now been solved.
Casio
A small number of late Casio phones are compatible with current exploits, such as the 930CA. Extracting data from other models will require an entirely new strain of research.
Fujitsu, Mitsubishi, Sharp
Fujitsu, Mitsubishi, and Sharp phones can all be booted into a special "Maker Mode" with additional permissions. We have figured out how to extract data from the JAVA folder in some of these phones, but have yet to take full advantage of this "Maker Mode."
Phones from these manufacturers generally use the SH-Mobile CPU chip.
Fujitsu
Current exploits for Fujitsu phones have worked with some models and not others. Issues likely stem from the ktdumper script requesting the wrong folder path. It will be difficult to fix this code for more Fujitsu phone models until more firmware dumps are provided. This requires desoldering the CPU BGA chip and putting it into a compatible chip reader.
These are the general ranges of models our current exploit works for, though many in-between models still need to be tested.
- F902i - F906i
- F884iES
- F-04A - F-10A
Mitsubishi
The situation with Mitsubishi phones is essentially the same as it is with Fujitsu phones.
These are the general ranges of models our current exploit works for, though many in-between models still need to be tested.
- D702i - D705i(myu)
- D902i - D905i
Sharp
We have successfully preserved one Sharp phone, the SH-03E, by reading its eMMC flash. This firmware has helped us derive the exploits to work with Fujitsu and Mitsubishi phones. Ironically, we have not been able to use these tools with Sharp phones yet. These phones can be booted into Maker Mode, but we still need to figure out what to do from there.
Sharp SH-10C
The Sharp SH-10C is a DoCoMo phone released in 2011. Attempts have been made to read the NAND chip on this phone, in part because its schematics were made public by the FCC. Currently, there are no chip programmers that support its NAND chip (Toshiba TY00D0021211KC) by default, and attempts at using a chip programmer have not reached past the bootloader. For more information, we recommend reading the report below.
- Report on Extraction of Data from DoCoMo Sharp SH-10C Mobile Phone by Kraze
- Sharp SH-10C on the Legacy Portable Computer Wiki
Others
LG
LG DoCoMo mobile phones had their firmware dumped at least 10 years ago, though most of these files have been lost. The firmware dumping process has not been replicated since, but should be possible to figure out with some research.
The following phones have had their firmware preserved:
Motorola
The Motorola M702iG and M702iS are based upon the Motorola Razr that was released internationally. Due to the availability of information about these phones, their firmware has successfully been accessed through USB. It's possible to browse the entire file system on these phones using a RMCDA General Program, M702iS/M702iG USB Drivers, and P2K Commander.
The following phones have had their firmware preserved:
- M702iG
- M702iS
Brute Force Live Stream: Cracking the Cryptomeria Cipher
THIS SECTION IS UNDER CONSTRUCTION AND IS NOT UP TO DATE.
General Summary

The microSD cards in Japanese feature phones hide copyright protected data using a Cryptomeria Cipher, also known as a C2. Cracking the C2 requires three things: s-box, device keys, and a game-specific bind ID.
- The S-BOX was discovered a few years ago within the firmware of a Japanese Samsung Galaxy S2 (it was used to encrypt live television recordings
- The
Having the s-box and device keys allows us to find the bind ID. The s-box was discovered last year, but hackers are still searching for phone specific device keys. These device keys can be used across multiple game dumps, so it's not necessary to find each device's set of device keys for decryption to work.
THE DEVICE KEY HAS BEEN FOUND THROUGH BRUTE FORCE.
With that in tow, we'll now get to the games: finding the game-specific bind ID using the device key and s-box (which has already been acquired). It depends on how long that will take, but the device key will make things exponentially easier than if we didn't have it. Next is to combine the three to decrypt the game files... and nobody knows what will happen next.
One of the main goals of this brute force effort is to access a specific SD card that contains Rockman DASH: Great Adventure on Five Islands!
- Video footage of Rockman DASH: Great Adventure on Five Islands!
- Cracking Rockman DASH: Great Adventure on Five Islands! Livestream
- Source code for MKB Bruteforce
Hardcore Summary
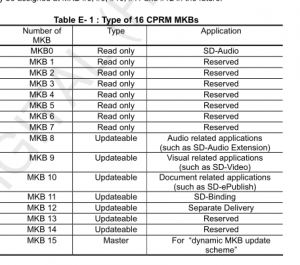
An MKB on SD cards generally contains two records (except some mostly irrelevant header records): Calculate Media Key and Conditionally Calculate Media Key.
- A row which corresponds to our device key is looked up in Calculate Media Key record.
- We decrypt this row with our device key, and get another key.
- In the Conditionally Calculate Media Key record, there's an encrypted block with a specific (constant) value which we attempt to decrypt with the key from the previous step.
- If this value matches what we expected, we look up a row in the Conditionally Calculate Media Key record (same row number as in step 1) and decrypt it with the key we got in step 2, then decrypt it again with the device key - that's our key; else we are done and the key is what we got in step 2.
We've made an assumption that the condition in step 4 is always true. Which isn't extremely unreasonable - values in the Conditionally Calculate Media Key record don't seem like what you would expect according to specification (if I've interpreted it correctly, invalid values would be identical to what is in the Calculate Media Key record; and they aren't). So as long as the assumption holds true, it'll eventually succeed.
For more technical information, please look at the following official PDFs:
- Content Protection for Recordable Media Specification: Introduction and Common Cryptographic Elements (PDF)
- Content Protection for Recordable Media Specification: SD Memory Card Book - Common Part (PDF)
- Content Protection for Recordable Media Specification: SD Memory Card Book - SD-Binding Part (PDF)
Archive Re-release Restoration Projects
This section will describe efforts to restore original DoJa game files.DoJa is a proprietary Java runtime developed by NTT Docomo to run specifically on feature phones. Games consist of two files: the .jam file (java manager file), which provides technical information to the phone about the application's install requirements, and the .jar file, which is the game itself. DoJa games use a scratchpad, which is saved as a .sp file.
Appli Archives for PlayStation Mobile
The Appli Archives are a series of feature phone re-releases. The PlayStation Mobile games contain DoJa files for each game, likely from original source. Game files and assets are drawn from a localhost server that runs within the PlayStation Mobile application. Because of use of localhost, these games cannot run directly in the DoJa SDK. However, some files have been made to run by hosting files on a localhost server on PC.
PlayStation Mobile game packages use PSSE encryption, which requires a game's original license key in order to perform decryption. Because of this, many of the Appli Archive files have not been decrypted, and their DoJa games have remained inaccessible.
Visit the Japanese Feature Phones wiki for the full list of games in this collection.
Mobile Game Deployer (MGD) and iαppli Publisher Games
Mobile Game Deployer/iαppli Publisher was a software that could easily convert i-mode applis into Android, iOS, and Windows Phone programs. A number of prominent feature phone game publishers used this tool to bring their games to the smartphone generation.
The game Flyhight Cloudia was successfully extracted from an Android APK in a fully playable version.
So far, other games have not been converted due to the difficultly in finding original application files for early smartphone games. Not only are these games approximately 10 years old, but they were often distributed in provider-specific mobile game portals, rather than common application stores such as Google Play and the App Store.
G-mode Archives
The G-mode Archives are a collection of Japanese feature phone re-releases for Nintendo Switch and Windows (Steam) published by G-mode. These games were developed in Unity, and so far no DoJa files have been discovered inside of them.
Emulating Network Protocol?
At this point, no one knows how to emulate the proprietary network protocols that were used by these mobile devices to download games. This means that no one has successfully added new applications or side-loaded applications to a Japanese feature phone. Even though a wifi enabled phone can access a website containing a game download, the wifi Full Browser does not offer the ability to download the game files. Only the proprietary browser (such as i-mode) has the capacity to download and install games.
Notable Japanese Feature Phone Games
Some notable titles from recognizable game series include:
- Before Crisis -Final Fantasy VII- and Dirge of Cerberus Lost Episode -Final Fantasy VII-: Games in the Final Fantasy VII metaverse that greatly expand upon its lore
- Professor Layton and the Mansion of the Deathly Mirror: A unique Professor Layton title released exclusively for Japanese mobile phones
- Kingdom Hearts coded: A story that covers events proceeding the finale of Kingdom Hearts II
- Persona Mobile Online: An entire Persona online MMORPG for cellphones
- Ni no Kuni: Hotroit Stories: A prologue to the Ni no Kuni series that takes place before Ni no Kuni: Dominion of the Dark Djinn
- Pokémate: The first Pokémon mobile game
- Nakayoshi Chao!: A Chao virtual pet game for phones
Resources
- Japan's Game Preservation Crisis by Did You Know Gaming
- Japanese Feature Phone Game Preservation: Uncovering a Forgotten Era of Gaming on HitSave.org
- Japanese Feature Phones Wiki (made by HM member Ellen!)
- Feature Phone Preservation Resources by Ellen
- Japanese Feature Phone PC Downloads posted on Archive.org